SYDNEY J. FREEDBERG JR.
 CRYSTAL CITY: Just when you thought the Pentagon’s new cloud strategy was all about adopting private sector practices, it makes an offhand reference to Armageddon. Cloud computing can swiftly switch users to different backup data centers around the country if one goes down, the strategy notes approvingly: “This will be vital in the case of human-made or natural destruction of a large geographic area.”
CRYSTAL CITY: Just when you thought the Pentagon’s new cloud strategy was all about adopting private sector practices, it makes an offhand reference to Armageddon. Cloud computing can swiftly switch users to different backup data centers around the country if one goes down, the strategy notes approvingly: “This will be vital in the case of human-made or natural destruction of a large geographic area.”That’s not the kind of contingency that private companies usually plan for. But this line and others in the cyber strategy – released Monday– should be a wake-up call for the tech sector that the military is a very different kind of customer with some uniquely challenging demands that require a different approach.
“It’s amazing what I get [that’s] just repackaged with a new label,” the same solutions over and over that won’t work on the front line, Marine Corps Brig. Gen. Dennis Cralltold an audience of contractors at the National Defense Industrial Association’s annual special operations conference. “You’re not looking at my mission needs.”
Brig. Gen. Dennis Crall testifies to Congress
War Clouds
“It’s not just about being rugged,” said Crall, the Pentagon’s senior uniformed military advisor for cyber policy. “It’s not about if it passes the drop test or it can be kicked around and submerged in 10 feet of water. Can it operate successfully in an information-contested environment,” when a sophisticated adversary – e.g. Russiaor China – is jamming your transmissions and hacking your network?
“If ‘there’s an app for that,’ does the app work when you’re disconnected?” Crall asked. “Does the app work when you haven’t had food for three days and you’ve been cut off?”
The answer is all too often “no” for standard commercial products – and much military technology, for that matter – that all require an uninterrupted, high-bandwidth connection. Even the Defense Department’s back-end business systems, like those that ship fuel worldwide or order spare parts from contractors, may come under a kind of sustained, sophisticated assault that Silicon Valley doesn’t usually have to deal with. And those support systems are increasingly connected to frontline tactical units that can’t just take their laptops to Starbucks and log on to the free wifi when their own network goes down.
The military, Crall told me after the panel, doesn’t want applications that are “chatty” – that only work when they can transmit “a tremendous amount of data back and forth” between the user in the field and some central server. (What he didn’t say out loud: That’s a pretty good description of a lot of cloud-based services). The military needs systems that can do at least some of their processing “at the tactical edge,” in devices small, light and power-efficient enough that the troops can carry them, and that troops can keep using in a stand-alone mode even when the network goes down.
On the flipside, Crall said, the military doesn’t want stand-alone solutions that work fine for a specific task – “they… could be wonderful,” he told me – but don’t connect well to the wider network. All too often, he said, industry offers products that can’t share data with other systems the military is already using, at least not without “constant care and feeding” by an already overburdened cyber workforce. And things that require labor-intensive kludges to function at the Pentagon or on a US base aren’t going to translate well to war zones, he warned: “If it’s clunky in garrison, it’s probably inoperable at the fighting edge.”
Now, Crall continued, when he makes this point to industry, they come back at him, quite rightly, with a demand of their own: “Okay, Crall, if you want that level of integration…. give me your standards so we can develop to those standards, [using] a standard developer’s toolkit.”
The Department is working on those standards now, he told me.
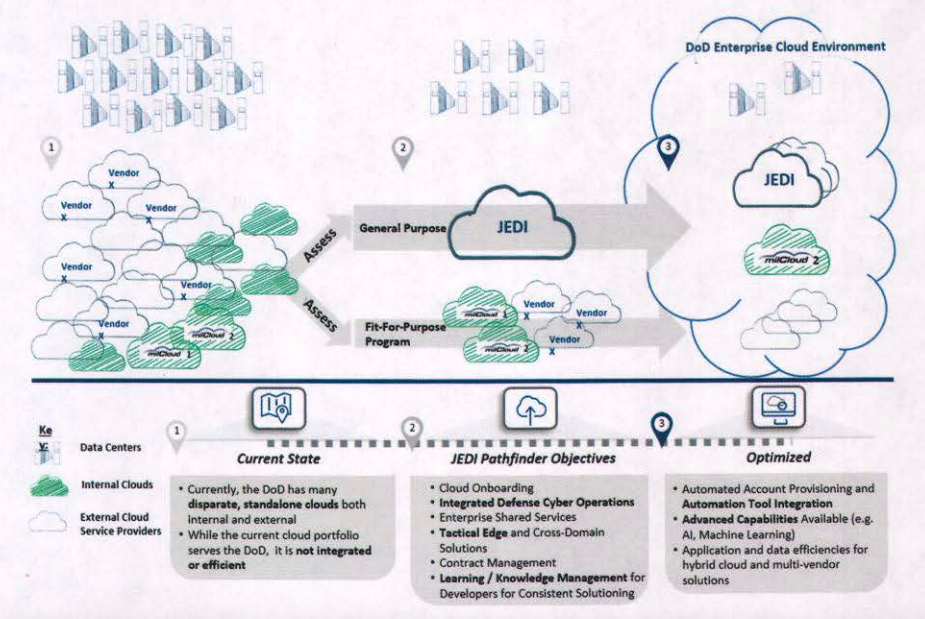
The Defense Department’s strategy to transition to cloud computing. Note the central role for JEDI (Joint Enterprise Defense Infrastructure)
Cloud Is Not Enough
Moving to cloud computing will help drive everyone to common standards that make everything work together, Crall told me, but the cloud alone is not enough. The individual software applications in that cloud environment have to be designed correctly, too. And in the longer term, he said, the third leg of the stool is Artificial Intelligence, which helps the cloud work better — and in turn, AI needs the cloud to work. You can’t train machine learning algorithms without access to huge amounts of data, he explained, and you can’t access that data when it’s scattered in a dozen incompatible databases, you need to pool it together in the cloud.
This is a tremendous technical challenge, and the military is under no illusions they can solve it with their in-house technical know-how – which the cloud strategy acknowledges is sadly lacking.
“As DoD has continued to stand up independent clouds, we continue to dilute our already constrained cloud expertise,” the strategy says. “The DoD oftentimes relies on outside contracting firms [and] decisions are being made at high levels without in-house technical expertise. [In particular], the specific requirements of securing a cloud environment will strain the traditional technical workforce and requires specialized skills where the Department currently has limited expertise.”
In the long run, “the Department must develop a cadre of technical professionals” – but the strategy says we have to get started now, which means relying on industry. “The Department has never built or implemented an enterprise cloud solution and therefore, recognizes the importance of finding a commercial partner to help begin the process.”
So, alongside the mentions of uniquely military needs — above all the need for the cloud to serve that frontline “tactical edge” — much of the strategy is a paean to the private sector:
Commercial cloud services will improve cybersecurity, the document says, because private-sector providers can quickly patch their software and replace their hardware whenever it’s proven vulnerable, something government struggles to do with systems that it owns and operates itself.
Commercial cloud can ramp up provide more computing power on demand, then ramp back down, so the Pentagon is neither limited by its own in-house hardware in when demand is high nor forced to pay for idle assets when demand is low.
Commercial cloud can track the costs of all of this second-by-second, while the Pentagon audit struggles to track down missing millions.
And, the strategy repeatedly says, the Pentagon must rely, at least “initially,” on the expertise of “a single provider…. a commercial partner” to stand up a “general purpose cloud” that will serve most military functions.
If you’ve followed the news on this, that’s a defense of the JEDI contract, on which Amazon Web Services is widely assumed to have a lock, despite protests from competitors and Congress.
Concentration Of Power
Just as there’s a concentration of power on the contractor side, in Amazon and the JEDI contract, the strategy also recommends a comparable concentration of poweron the government side. (As we wrote seven years ago, when you move from every office having its own server in a closet somewhere to a shared cloud, you inevitably centralize power).
The main body of the document repeatedly mentions the need for a strong hand – to maintain oversight of the equally strong “single provider,” to set common standards and processes, to assess all the data on what individual defense agencies are doing. But it’s only in “Appendix A: Implementation Details” that the strategy gets specific: “Oversight and governance for the initial build out of this enterprise cloud strategy will be led by the Office of the DoD CIO.”
That’s the Pentagon’s Chief Information Officer, Dana Deasy. As we put it last week, recent legislation has given Deasy & co. “the authority to crack heads together and impose common cybersecurity standards.” Crall got a lot of emails about that article, he told me.
“I chuckled at the cracked-heads piece because I think we’re a more collaborative, cooperative group, but your point was well taken — that the CIO has new-found authorities that are directive in nature, so we can move at greater speed,” Crall told me.
“He certainly values the input of the services and the Fourth Estate” – the various defense agencies – “to make sure we’re making good decisions, Crall said. But Deasy “is absolutely driving it… We’re moving out.”